Experience,
Served in Best Balance

Safest Economic Solution
Better Price & Quality
By Cloud Based Analysis
Protection via Pre-Detection
Watch It Below
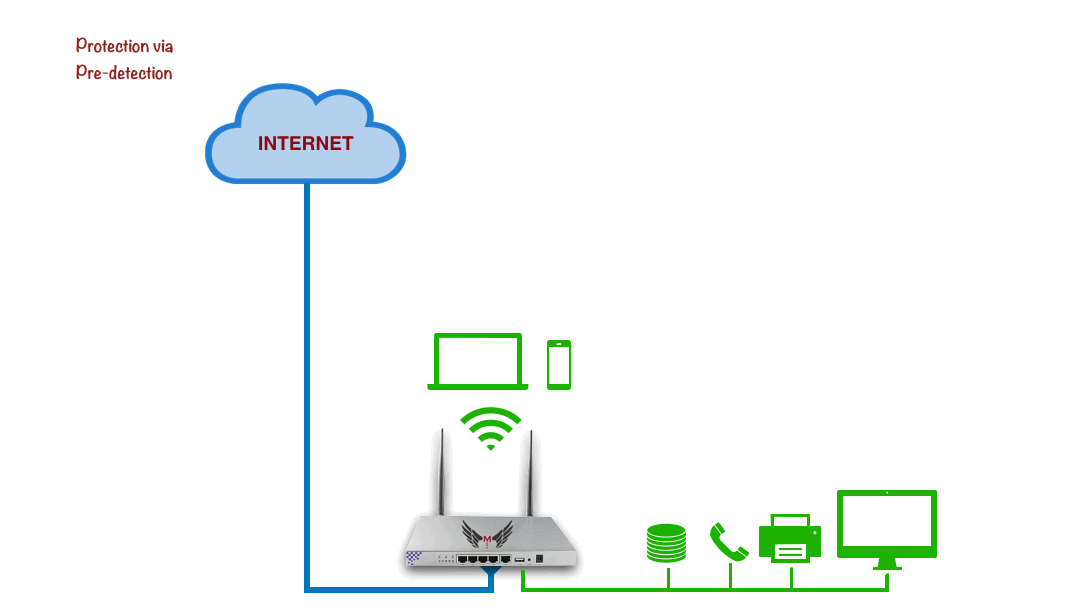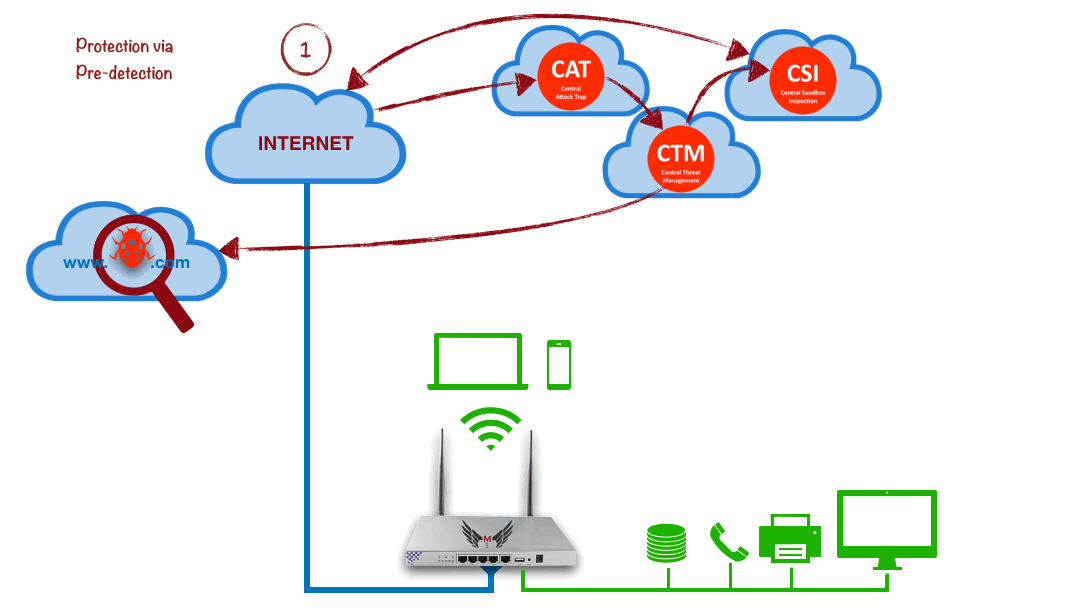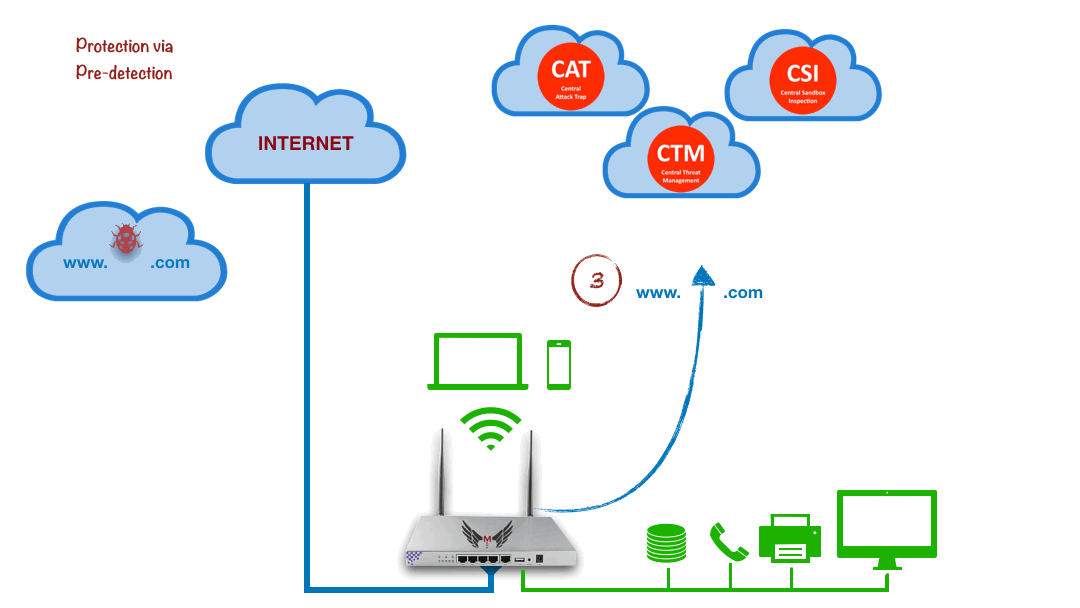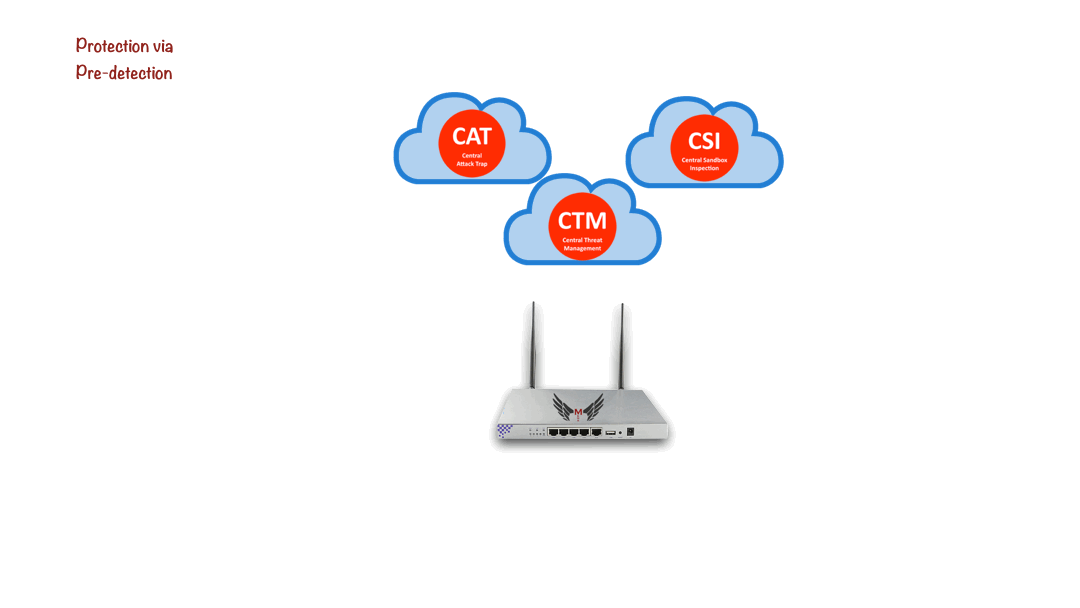
Cloud Analysis, Local Prevention
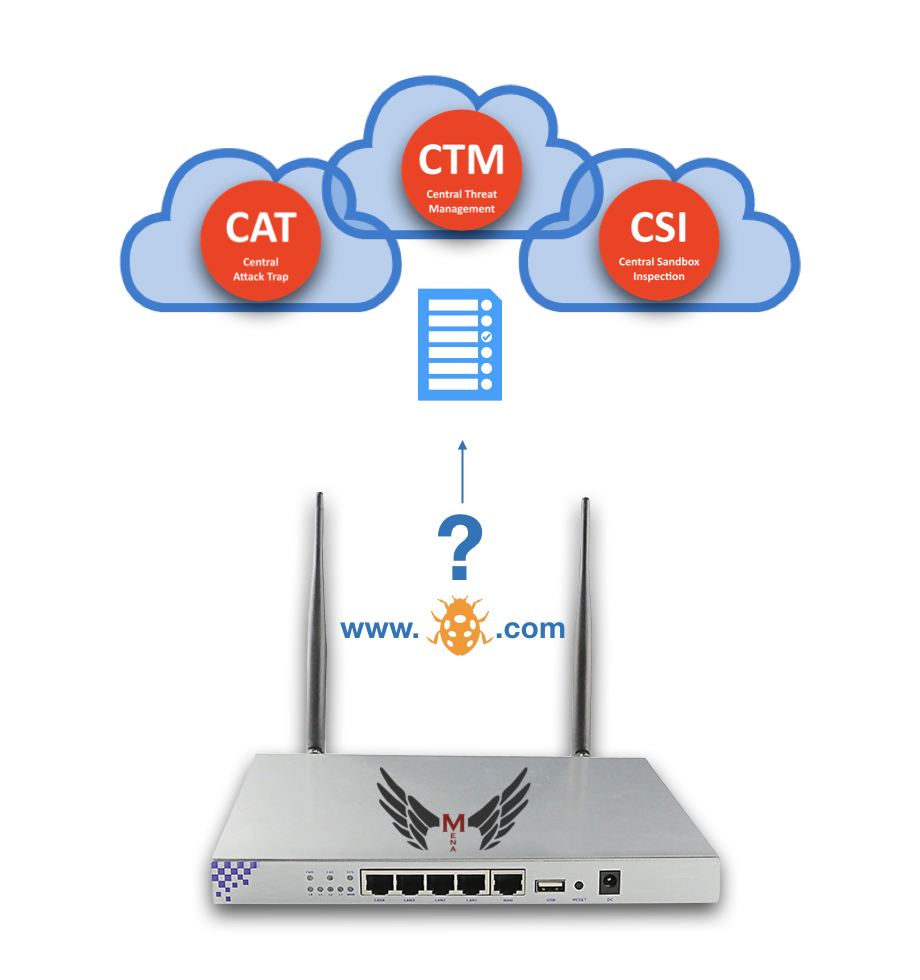
Cloud Systems

-
Continuously Analysis Internet Born Threats
-
Enables Up To Date Information of Threat Addresses
-
Does Not Need To Track Your Connection
-
Finds Out Phishing Attack Centers
-
Finds Out Malware Servers
-
Prevents Internet Based Recent Attacks
Local Device
-
Without Tracking Your Traffic
-
By Asking It to Cloud
-
Protects You Before Visiting A Harmful Site
-
Provides OpenWRT, Freedom Of Open Source Programming
-
Use Our Simplified Menus or Use Any Feature of OpenWRT

“Smart” Defence
Inspection, Detection, Prevention:
All Actions, Fully Automized
Created by Cyber Security Experts


25+ years experience in IT and security, 13 years with OSCP (Offensive Security Certified Professional) and 12 years with OSCE (Offensive Security Certified Expert) certificates, 12 years of experience on ISR R&D Labs.
Celebrating
2nd Year
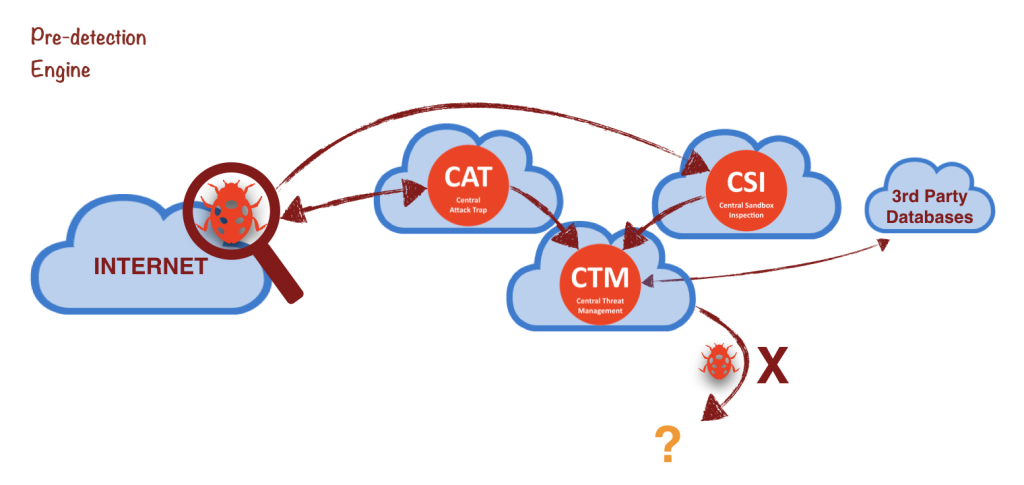
Pre-detection Engine
&
Mena
Latest Threat Database
Delivered
In Most Simple Form Possible
Simplified With AI, For Your Needs:
 – Tracking and Applying Threat Databases : Inspecting online databases, evaluating the threats and selecting and applying the necessary rules to prevent threats is a must for a security employee. There are a few challenges; one of them is doing it as soon as possible, so the intruders won’t be able to use known threats against you, and second challenge is to do it 24 hours a day in whole 7 week days, whole year (!), without stopping. It ain’t a human’s job, right? We covered it.
– Tracking and Applying Threat Databases : Inspecting online databases, evaluating the threats and selecting and applying the necessary rules to prevent threats is a must for a security employee. There are a few challenges; one of them is doing it as soon as possible, so the intruders won’t be able to use known threats against you, and second challenge is to do it 24 hours a day in whole 7 week days, whole year (!), without stopping. It ain’t a human’s job, right? We covered it.
 – Tracking News and Applying Preventions : Inspecting online news and events that are not currently converted into databases, evaluating the threat causes, turning them into an action data and applying the necessary rules to prevent similar threats, is a hard and necessary job, it prevents you from both advanced threats, zero-day attacks and from early rising viruses. Same humanity challenge goes here; doing it as soon as possible, and doing it 24/7 without stopping. We got it covered.
– Tracking News and Applying Preventions : Inspecting online news and events that are not currently converted into databases, evaluating the threat causes, turning them into an action data and applying the necessary rules to prevent similar threats, is a hard and necessary job, it prevents you from both advanced threats, zero-day attacks and from early rising viruses. Same humanity challenge goes here; doing it as soon as possible, and doing it 24/7 without stopping. We got it covered.
 – Tracking Roaming Files and Inspecting Local Files : Although using different detection systems for file-based attacks by e-mail filters, firewall spam filters, antivirus scanners etc. still, files are complicated threats in a network environment. In order to eliminate file threats, you still have to track roaming files in Internet, classify them as harming / unharming clean files, even detect their true intention (!) because they can be coded for hiding harming intention. It is a team job actually, which we also covered it.
– Tracking Roaming Files and Inspecting Local Files : Although using different detection systems for file-based attacks by e-mail filters, firewall spam filters, antivirus scanners etc. still, files are complicated threats in a network environment. In order to eliminate file threats, you still have to track roaming files in Internet, classify them as harming / unharming clean files, even detect their true intention (!) because they can be coded for hiding harming intention. It is a team job actually, which we also covered it.
 – Hyperactive Threat Inspection : Determining a recently started attack; gathering it’s details and applying prevention just before it spreads? It is a security pro-work. We got it covered.
– Hyperactive Threat Inspection : Determining a recently started attack; gathering it’s details and applying prevention just before it spreads? It is a security pro-work. We got it covered.
Mena MSV Series
Practical, Scalable,
Served In A Way
You Get Used To

FEATURES
– 300 Mbps, 2.4 GHz Wireless power –
– Virus, Trojan, Malware, Phishing Protection –
– Honeypot Protection –
– Cyber Intelligence, DNS Protection, Wide Database Protection –
COMPATIBLE WITH ETHICS
GDPR
- Mena will support your responsibilities under the law and ethics, ensure that cyber security is taken on the site.
- Personal data is not monitored, neither examined nor stored during Mena file analysis.
27001 – Information Security Management Systems Compatible
- It is suitable for use in the context of information security management systems.
- Is one of the most important assistant in you ISMS.
- As a successful layer of security, it allows you to fulfill your responsibilities and elevate your standards.
MALICIOUS TRAFFIC BLOCKING
Virus
- Viruses are not only on personal computers, but also seen on all devices connected to Internet.
- Mena, blocks viruses before they reach you.
- If you have infected devices, Mena will protect data theft from this devices.
- Mena, stops viruses to slow down your connection and spreading viruses to others.
Trojan
- Trojan is a type of virus which spreads malicious software by using back doors.
- Mena, stops extending and widening of trojans.
Malware
- Malware, even seems as a normal software at the beginning, carries its harms in time and enables harmful consequences as a virus.
- Mena, effectively prevents most of the malware, prevents malware reaching by the Internet.
Phishing
- Phishing is the type of attacks that are trying to con people. They intend to get either your valuable information or without permission, use your device resources to attack anywhere else.
- It is a very dangerous attack type which may lead to theft of your personal data, theft of your money or use of your resources in a crime event without your permission.
- Mena, actively struggles with phishing attacks by it’s wide database and continuous scanning sources and protects you.
DID YOU KNOW?
Mevertech is the authorized reseller of cyber attack protection appliance MENA which is a practical and a successful intermediate level solution.

STRONG CYBER INTELLIGENCE
4 Continents
- Worldwide placed traps of Mena enables advance notices of cyber attacks.
- After the attacks begin anywhere in the world, sources of attacks are determined and Mena starts protecting you against these.
- Even before dawn, Mena identifies the world’s attack trends, allowing you to start your day ready against them.
5 Sectors
- Trap mechanisms established in various sectors and manipulative attackers are bait and lured.
- Provides significant and successful detection of the attacks initiated with financial interest.
8 Trap Types
- Different traps are established against various curious and manipulative attackers.
- These traps, which are established for different types of services, also vary according to the tendencies of attackers and this increases trap success.
EXTENSIVE KNOWLEDGE BASE
Many Years of Experience
- The experience of the ISR Information Security Team is based on the 1990s.
- All existing and new team members always have an active view of research and development.
- It offers it’s knowledge in all projects completed on new products and projects in order to achieve better ones.
200.000+ Servers
- Mena follows the harmful servers in an active and evolving database.
- Continuously follows the addresses that are active in the crime, cleansed victim servers and the erroneous parsing will be rapidly restated.
- Hundreds of new servers are automatically entered into their database every day.
15 Million+ File
- Automated analysis and follow-ups improves the file knowledge base continuously.
- Closely follows worldwide file lists, analyzes, parses erroneous lists and inspects the suspicious files.
122 Million+ Threats
- It has millions of threat information that has been identified in many different areas.
- In the recent years of cybercrime, the increase in databases has successfully captured the speed of growth, detecting new servers fairly rapidly and preventing threats on time.
MODEL SELECTION

MODEL NAME |
CAPACITY |
HARDWARE* |
PRICE** |
| MSV1es | Small | MSV1e | – € |
| MSV1em | Medium | MSV1e | – € |
| MSV1el | Large | MSV1e | – € |
* All models require purchase of an annual license for cyber security features. License fees for MSV1e models are 20% of the current list price of the model.
** Prices are indicative and may vary according to regions and vendors. Current prices are valid at the time of purchase.

MODEL NAME |
CAPACITY |
HARDWARE* |
PRICE** |
| MSV2es | Small | MSV2e | N/A-€ |
| MSV2em | Medium | MSV2e | N/A-€ |
| MSV2el | Large | MSV2e | N/A-€ |
* All models require purchase of an annual license for cyber security features. License fees for MSV2e models are 20% of the current list price of the model.
** Prices are indicative and may vary according to regions and vendors. Current prices are valid at the time of purchase.
We Are Authorized Reseller!
TECHNICAL SPECIFICATIONS
| HARDWARE | MSV1e |
| MAIN CHIPSET | Atheros9531/550Mhz |
| RAM / FLASH | DDR1 128MB / SPI 16MB |
| PROTOCOL | IEEE 802.11n,IEEE 802.11g,IEEE 802.11b, IEEE 802.3, IEEE 802.3u |
| WIRELESS SUPPORT / SPEED AND FREQUENCY | Yes / up to 300Mbps, 2.4GHz, 2 * 5dBi Omni Antenna |
| INTERFACE | 1*10/100M WAN port(Auto MDI/MDIX), 4*10/100M LAN port (Auto MDI/MDIX),1*DC Power, 1*USB2.0 interface |
| BUTTONS / LED | 1*RESET / PWR, WLAN, SYS.WAN, LAN1, LAN2, LAN3, LAN4 |
| POWER | DC9V/1A |
| Size (L*W*H) / Package Size (L*W*H) | 235*165*22mm / 330*232*60mm |
| SOFTWARE | |
| OPERATING SYSTEM | openWRT |
| CYBER PROTECTION | Virus, Trojan, Malware, Phishing Protection, Honeypot Protection, DNS Protection, Wide database protection, |
| LEGAL COMPLIANCE | GDPR |
| OPERATING MODE | AP, Router |
| WAN TYPE | PPPoE, Dinamic IP, Static IP |
| DHCP | DHCP Server, DHCP Client List, Address Reservation |
| VIRTUAL SERVER | Port Triggering, DMZ |
| WIRELESS SECURITY | Client Filter, MAC Address Filter, WEB management |
| OTHER TECHNOLOGIES SUPPORTED | Syslog Support, Static Router, Web Theme Support, MAC cloning, NTP synchronisation |
TECHNICAL SPECIFICATIONS
| HARDWARE | MSV2e |
| MAIN CHIPSET | Atheros9531/550Mhz |
| RAM / FLASH | DDR2 128MB / SPI 16MB |
| PROTOCOL | IEEE 802.11n,IEEE 802.11g,IEEE 802.11b, IEEE 802.3, IEEE 802.3u |
| WIRELESS SUPPORT / SPEED AND FREQUENCY | Yes / up to 900Mbps, 2.4GHz/5GHz, 4 * 5dBi Omni Antenna |
| INTERFACE | 1*10/1000M WAN port(Auto MDI/MDIX), 4*10/1000M LAN port (Auto MDI/MDIX),1*DC Power, 1*USB2.0 interface |
| BUTTONS / LED | 1*RESET / PWR, WLAN, SYS.WAN, LAN1, LAN2, LAN3, LAN4 |
| POWER | DC9V/1A |
| Size (L*W*H) / Package Size (L*W*H) | 235*165*22mm / 330*232*60mm |
| SOFTWARE | |
| OPERATING SYSTEM | openWRT |
| CYBER PROTECTION | Virus, Trojan, Malware, Phishing Protection, Honeypot Protection, DNS Protection, Wide database protection, |
| LEGAL COMPLIANCE | GDPR |
| OPERATING MODE | AP, Router |
| WAN TYPE | PPPoE, Dinamic IP, Static IP |
| DHCP | DHCP Server, DHCP Client List, Address Reservation |
| VIRTUAL SERVER | Port Triggering, DMZ |
| WIRELESS SECURITY | Client Filter, MAC Address Filter, WEB management |
| OTHER TECHNOLOGIES SUPPORTED | Syslog Support, Static Router, Web Theme Support, MAC cloning, NTP synchronisation |


