Latest Technology
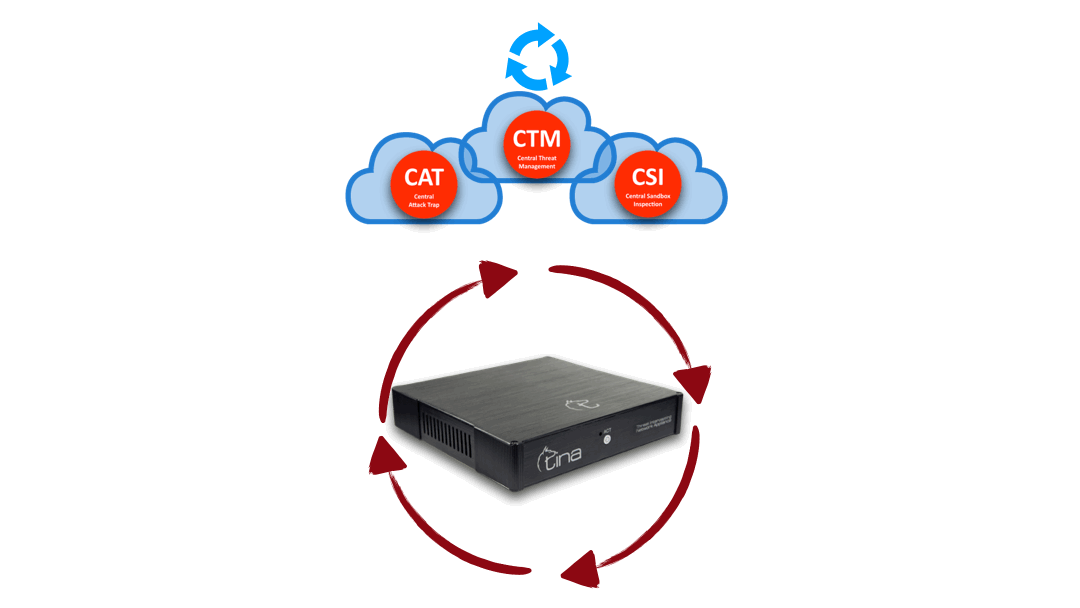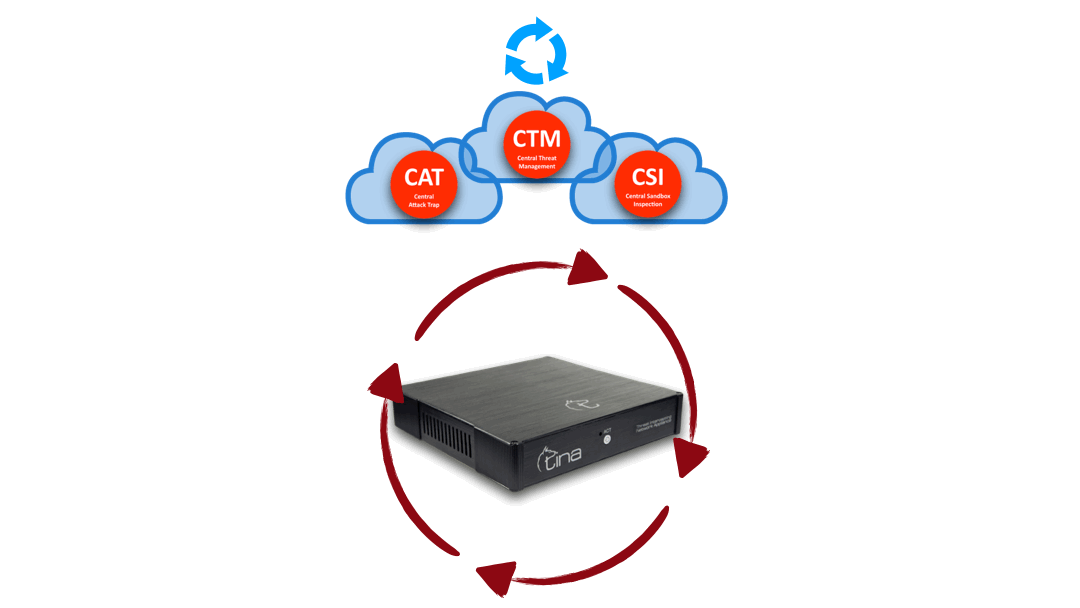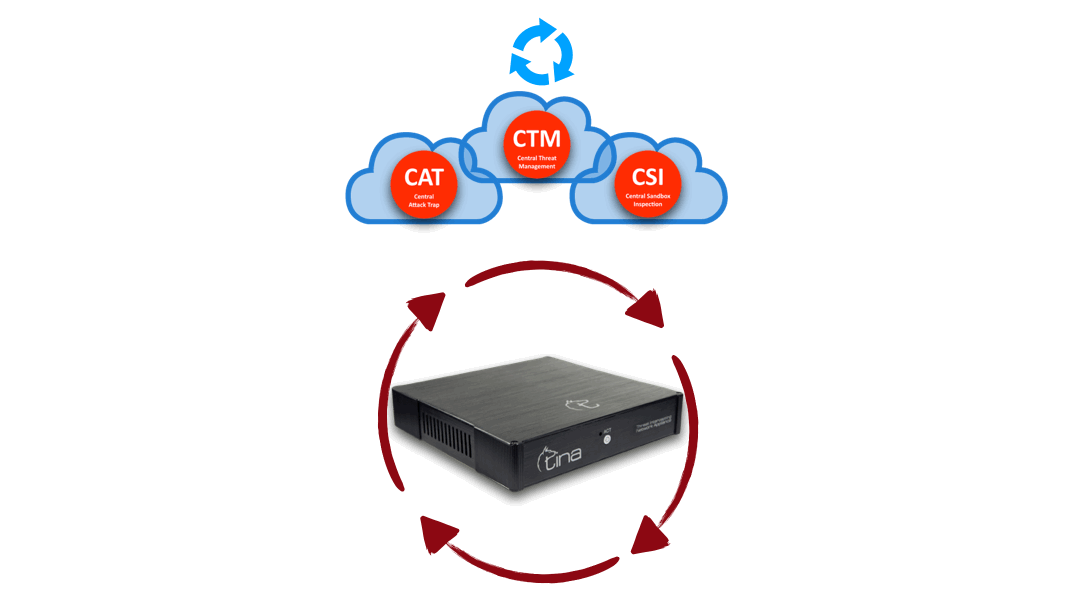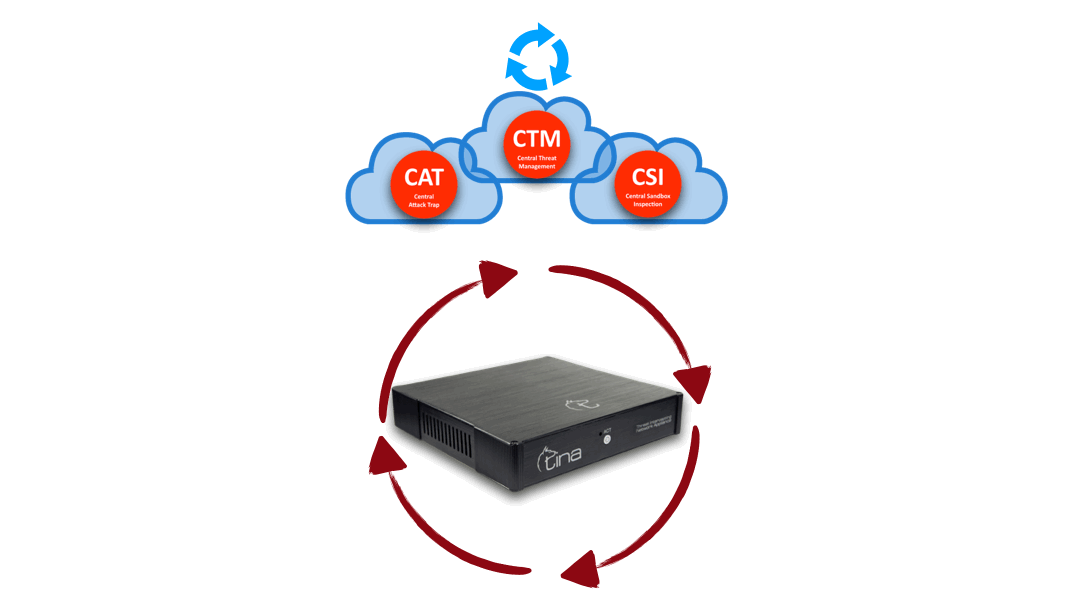
Hybrid Structure and Automated Protection
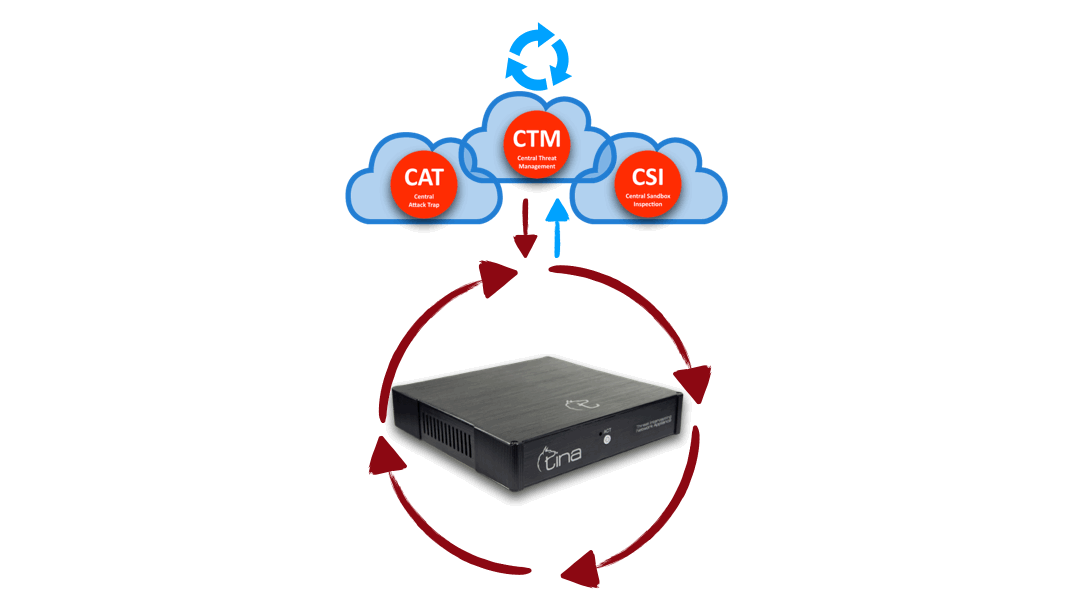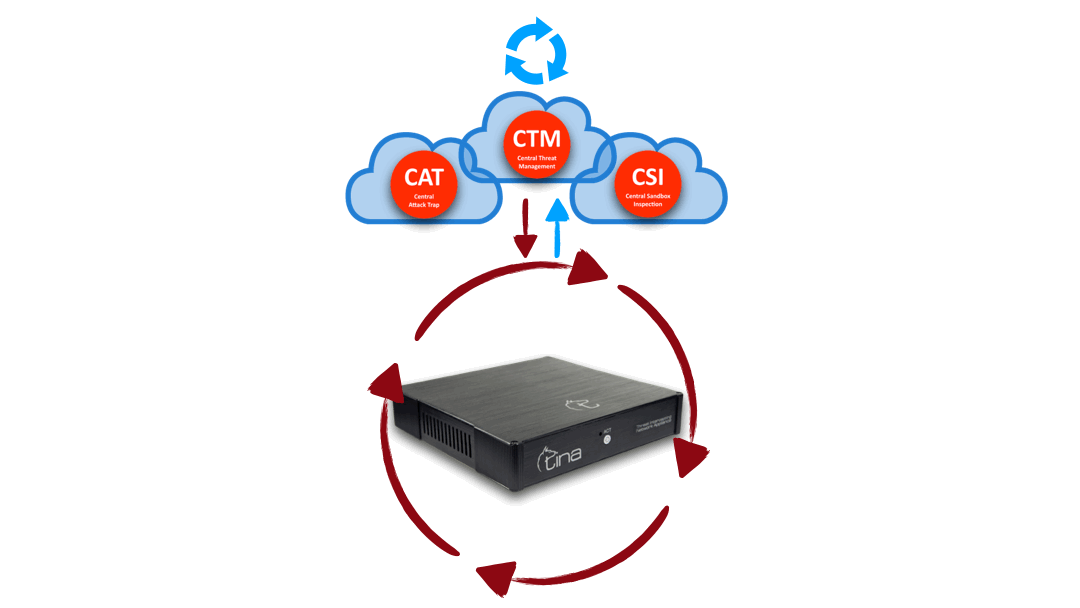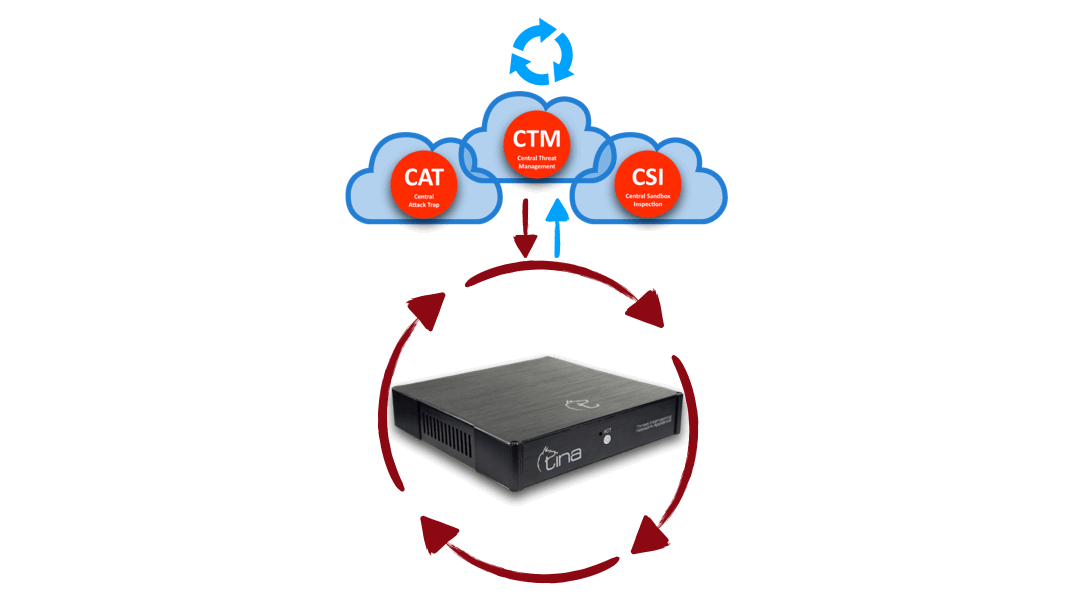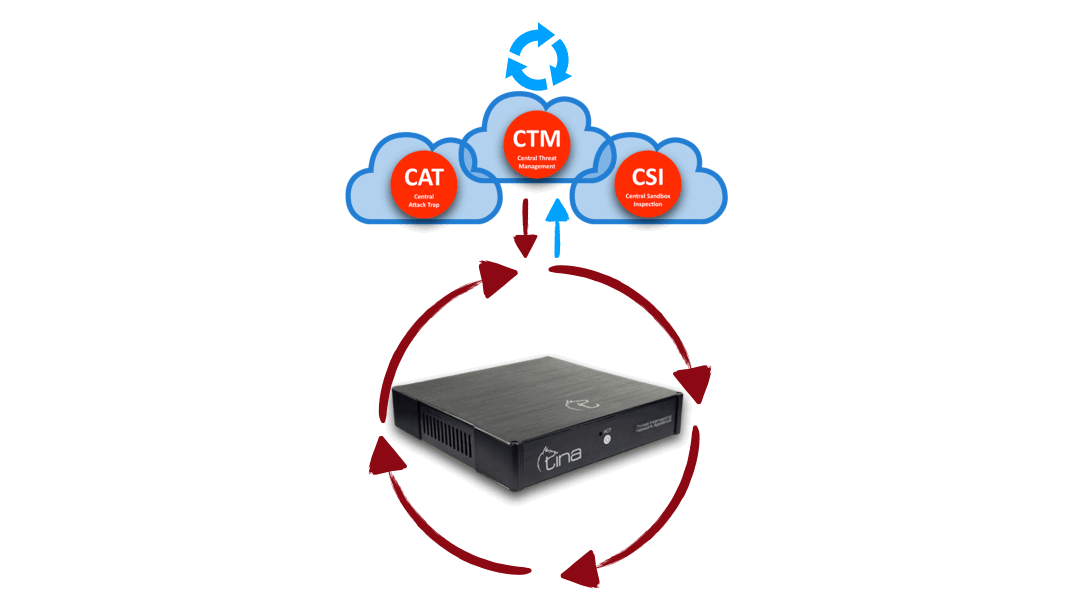
Hybrid Structure
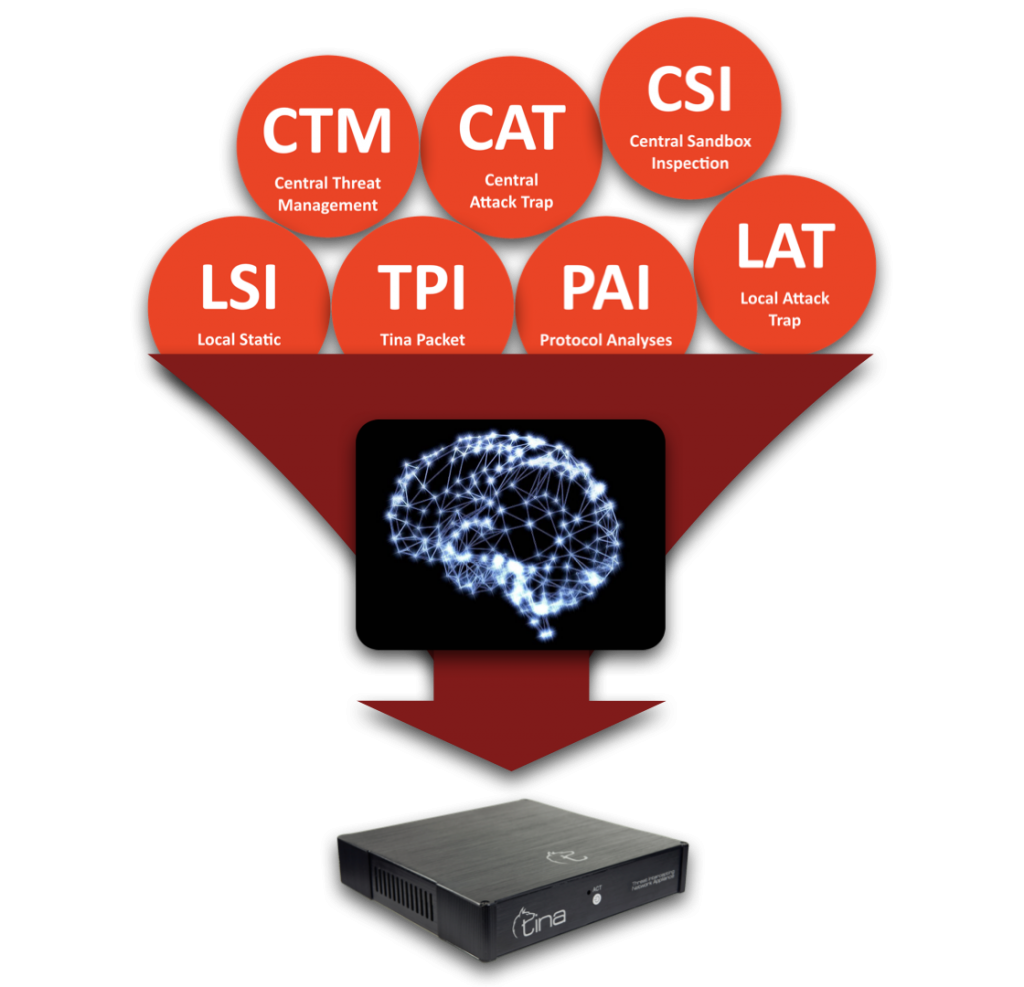
Central and Local Analysis
Hybrid structure enables TINA AI to do multiway analysis:
Stand alone; on premise, on CTM, separately
Hybrid; both on premise and CTM; requesting additional analysis from each other system
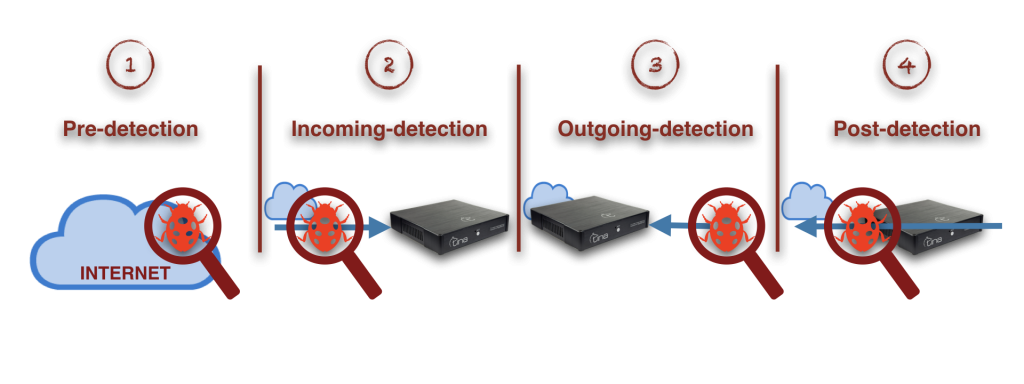
“Multi-stage” Defence
Active Analysis
on All “3+1” Stages
“Smart” Defence
Inspection, Detection, Prevention:
All Actions, Fully Automized
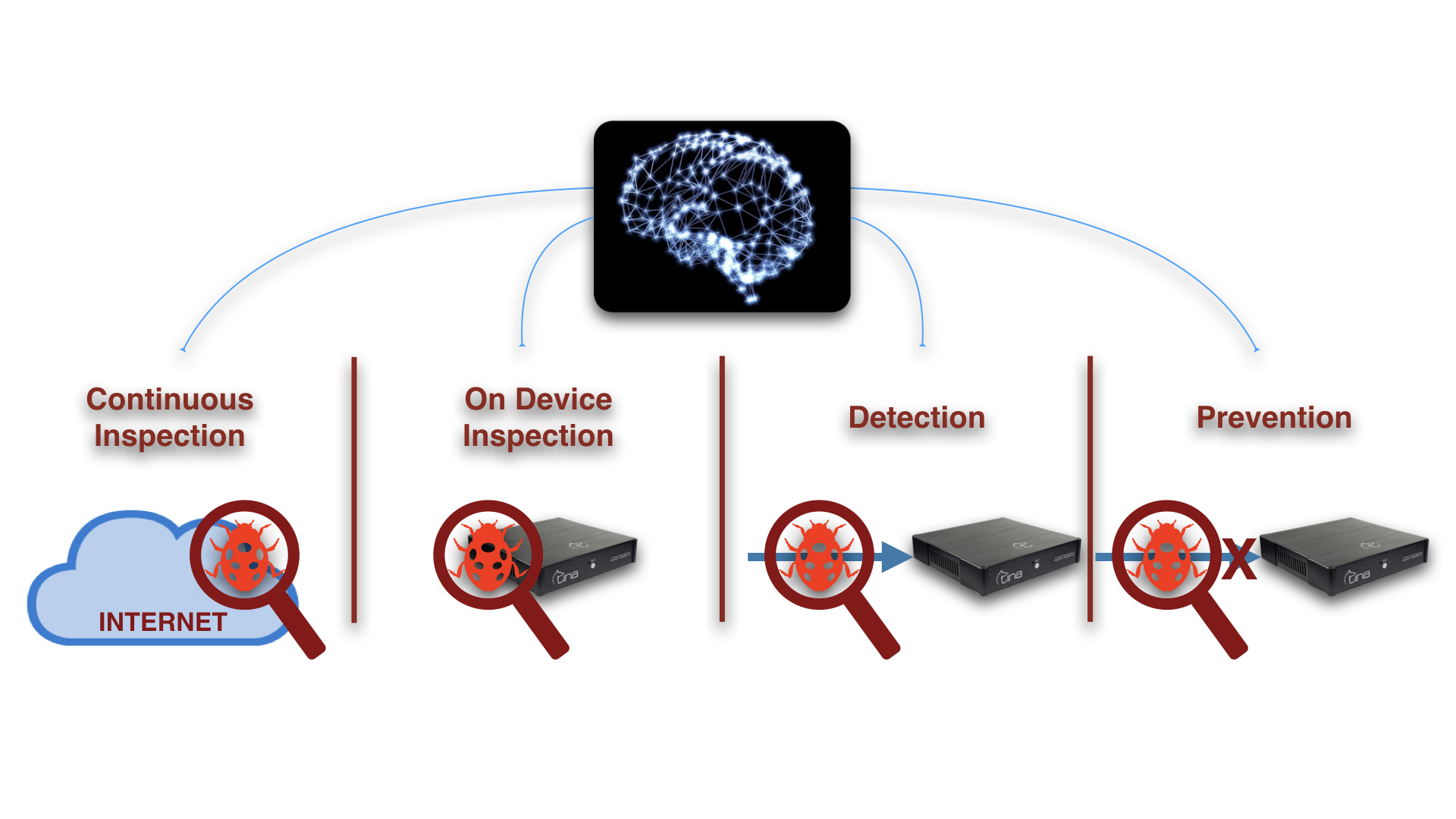

Fully Automized TINA AI:
Hybrid Structure: “Central” + “On Device” interactive & multiway analysis
Hybrid Analysis: “Central” + “On Device” advanced & stronger analysis
Machine Learning Powered: Central machine learning threat database
Cyber Threat Intelligence: Central & fully connected neural network database
Active Security: Fully automated decision making and prevention
Created by Cyber Security Experts


25+ years experience in IT and security, 13 years with OSCP (Offensive Security Certified Professional) and 12 years with OSCE (Offensive Security Certified Expert) certificates, 12 years of experience on ISR R&D Labs.
Celebrating
10th Year
Against
Advanced Persistent Threat*
Advanced Persistent Threat
Against Hide and Seek Playing,
Persistent, Tacky Malicious Codes

What An APT Does, In a Few Words
APT (Advanced Persistent Threat) is the most dangerous type of malicious codes. Even capable of hiding itself, like hide and seek game play, whenever you try to seek it, it hides. It is not easy to find and furthermore after finding it, is not easy to eliminate the defect of it. It is a tacky code that can reborn from the ashes.
APT cannot be detected by virus programs. They are not easily found in security literatures, virus databases, this is why in most cases user finds out an APT by their damages or suspicious anomalies, it does not leave a touchable clue. APT is sometimes very well designed for the target, it might be coded for a special purpose and a victim (person or company) does not even recognize their presence over a year or more!
Many of the (lucky) users use the same similar words when an APT is living on the digital grounds; “an unusual thing” happens, “something costs more”, “something slows down”, or “some how” “computer lives it’s own life!”
Mostly, a user finds out an APT by their damages; either after paying by reputation damage from stolen sensitive data, or peaking performance / resource problems by means of data load, CPU or any other resources cost as money lost.
Defining The Undefined
Most of the time APT cannot be detected by virus programs and user finds out an APT by their damages or suspicious anomalies, that does not leave a touchable clue.
Eliminating Future Problems
APT leads to undetected data theft and have a very long life span in a digital environment.

DID YOU KNOW?
Mevertech is the authorized reseller of APT protection appliance TINA which is an automated high level solution for Advanced Persistent Threats, Zero Days and signatureless attacks, besides any other known viruses and threat vectors.
Tina is also capable of detecting already placed APTs, zero days, or exploited software vulnerabilities. It is a hybrid system including many detection and protection techniques such as; network behavior analysis, malicious databases, AI, central database and central threat analysis labs, automated reverse engineering malicious file analysis, threat intelligence and active honeypot systems.
Let’s Work Together on Advanced Persistent Threat Protection!
TINA Technologies
Latest Technologies
Delivered
In Most Simple Form Possible
Simplified With AI, For Your Needs:
 – Tracking and Applying Threat Databases : Inspecting online databases, evaluating the threats and selecting and applying the necessary rules to prevent threats is a must for a security employee. There are a few challenges; one of them is doing it as soon as possible, so the intruders won’t be able to use known threats against you, and second challenge is to do it 24 hours a day in whole 7 week days, whole year (!), without stopping. It ain’t a human’s job, right? We covered it.
– Tracking and Applying Threat Databases : Inspecting online databases, evaluating the threats and selecting and applying the necessary rules to prevent threats is a must for a security employee. There are a few challenges; one of them is doing it as soon as possible, so the intruders won’t be able to use known threats against you, and second challenge is to do it 24 hours a day in whole 7 week days, whole year (!), without stopping. It ain’t a human’s job, right? We covered it.
 – Tracking News and Applying Preventions : Inspecting online news and events that are not currently converted into databases, evaluating the threat causes, turning them into an action data and applying the necessary rules to prevent similar threats, is a hard and necessary job, it prevents you from both advanced threats, zero-day attacks and from early rising viruses. Same humanity challenge goes here; doing it as soon as possible, and doing it 24/7 without stopping. We got it covered.
– Tracking News and Applying Preventions : Inspecting online news and events that are not currently converted into databases, evaluating the threat causes, turning them into an action data and applying the necessary rules to prevent similar threats, is a hard and necessary job, it prevents you from both advanced threats, zero-day attacks and from early rising viruses. Same humanity challenge goes here; doing it as soon as possible, and doing it 24/7 without stopping. We got it covered.
 – Tracking Roaming Files and Inspecting Local Files : Although using different detection systems for file-based attacks by e-mail filters, firewall spam filters, antivirus scanners etc. still, files are complicated threats in a network environment. In order to eliminate file threats, you still have to track roaming files in Internet, classify them as harming / unharming clean files, even detect their true intention (!) because they can be coded for hiding harming intention. It is a team job actually, which we also covered it.
– Tracking Roaming Files and Inspecting Local Files : Although using different detection systems for file-based attacks by e-mail filters, firewall spam filters, antivirus scanners etc. still, files are complicated threats in a network environment. In order to eliminate file threats, you still have to track roaming files in Internet, classify them as harming / unharming clean files, even detect their true intention (!) because they can be coded for hiding harming intention. It is a team job actually, which we also covered it.
 – Hyperactive Threat Inspection : Determining a recently started attack; gathering it’s details and applying prevention just before it spreads? It is a security pro-work. We got it covered.
– Hyperactive Threat Inspection : Determining a recently started attack; gathering it’s details and applying prevention just before it spreads? It is a security pro-work. We got it covered.
 – Live Traffic Analysis : Inspecting a traffic without violating user privacy is a sensitive issue. Without gathering all the user traffic information and analyzing user trends, which is a violation of privacy ethics, we do analyze connection protocol behaviors and following created unintentional connections towards an Internet address. It doesn’t matter if it is a new site or a cached site, even it isn’t included in any databases, a recently started traffic is analyzed on the fly; without privacy violation, and determined either intentional or unintentional connection. It is a security pro-work. We got it covered.
– Live Traffic Analysis : Inspecting a traffic without violating user privacy is a sensitive issue. Without gathering all the user traffic information and analyzing user trends, which is a violation of privacy ethics, we do analyze connection protocol behaviors and following created unintentional connections towards an Internet address. It doesn’t matter if it is a new site or a cached site, even it isn’t included in any databases, a recently started traffic is analyzed on the fly; without privacy violation, and determined either intentional or unintentional connection. It is a security pro-work. We got it covered.
 – Attacker Call-Back Traffic Analysis : Determining a traffic started unintentionally and/or without user knowledge even hiding itself in many ways; we can detect it. It doesn’t matter if it is a known hacker traffic, included in any databases, or an unknown zero-day attack, without privacy violation, we are ready to analyze it automated and on the fly. It is a security pro-work. We got it covered.
– Attacker Call-Back Traffic Analysis : Determining a traffic started unintentionally and/or without user knowledge even hiding itself in many ways; we can detect it. It doesn’t matter if it is a known hacker traffic, included in any databases, or an unknown zero-day attack, without privacy violation, we are ready to analyze it automated and on the fly. It is a security pro-work. We got it covered.
 – Attacker On Initial Phase Prevention : Even all of your prevention techniques and detection techniques fail; we do help for fighting back! An attacker after infiltrating to the network needs to map it; finding valuable server assets or stating the size of a network, we are there to confuse and stop the attack. We can detect mapping intentions and prevent it. Furthermore, we analyze the traffic back to the attacker and stop sequel traffic on the fly. We got it covered.
– Attacker On Initial Phase Prevention : Even all of your prevention techniques and detection techniques fail; we do help for fighting back! An attacker after infiltrating to the network needs to map it; finding valuable server assets or stating the size of a network, we are there to confuse and stop the attack. We can detect mapping intentions and prevent it. Furthermore, we analyze the traffic back to the attacker and stop sequel traffic on the fly. We got it covered.
Let’s be honest, we all can fail!
Attacker On The Job Prevention

– Attacker On The Job Prevention : Let’s be honest, we all can fail! Thinking of a failure is not a nice thing, but it happens, right? An advanced hacker, bypassing all of your software and hardware precautions, can clearly enjoy a successful theft, not if TINA is placed there! We are failsafe! We can even detect a post-hacking traffic after a successful exploitation, find the leakage source, identify it’s traffic details and stop it. We got it covered, we do fight back, what a technology right!
Want to see more technical details about TINA? Find further details below…
Meet Our
Technology
Orchestra
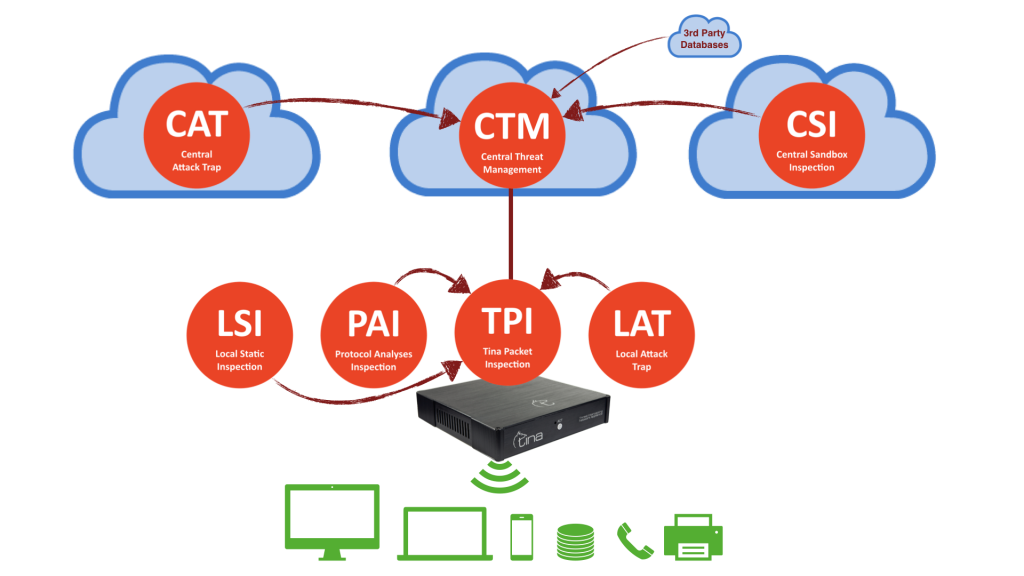
Own, Unique Technologies Coded
TINA has developed it’s own codes for detection technologies.
By this way, a cyber threat is analyzed much faster and in better harmony. All technologies are not dependent to each other but fully compatible with each other, can feed any other with data.
Works Altogether
TINA technologies have been created for a hybrid defence structure. Multi-staged defence surface includes external resource analysis, internal resource analysis, with an AI combined “analysis, decision and action” system.
All main technology systems have their subsystems. Furthermore; subsystems are both “a piece of the bigger system” and “a system alone”; they can run theirselves and decide by itself, also can feed data to other TINA systems or ask for help on further analysis when decided necessary.
C TM – Central Threat Management
TM – Central Threat Management
What we serve with TINA CTM and it’s subsystems are stated below.
– Tracking and Applying Threat Databases : Inspecting online databases, evaluating the threats and selecting and applying the necessary rules to prevent threats is a must for a security employee. There are a few challenges; one of them is doing it as soon as possible, so the intruders won’t be able to use known threats against you, and second challenge is to do it 24 hours a day in whole 7 week days, whole year (!), without stopping. It ain’t a human’s job, right? We covered it.
– Tracking News and Applying Preventions : Inspecting online news and events that are not currently converted into databases, evaluating the threat causes, turning them into an action data and applying the necessary rules to prevent similar threats, is a hard and necessary job, it prevents you from both advanced threats, zero-day attacks and from early rising viruses. Same humanity challenge goes here; doing it as soon as possible, and doing it 24/7 without stopping. We got it covered.
CTM Subsystems
CTM Update
- Central database that contains harmful resource information and all threat analysis
- Performs data base updates 7/24 automatically
- Updates the entire TINA; performs database and software updates automatically
CTM Notification
- Centre of alerting feature
- Provides periodic reporting
CTM Management
- Device overview screen (dashboard)
- Provides instant reporting
- Unlimited log storage capacity
- Provides device management via Web
CTM SIEM
- Module that enables log sharing via API
- Compatible with multiple systems; provides easy setup, can be matched with SIEM
CTM Multidevice
- Combines multiple devices into one account
- Provides a single interface for tracking multiple devices
- Enables reporting and commanding of each devices separately
CTM Technical Specifications
It has more resources than you can consume!
We won’t give you exact numbers, sorry, but let us give a little clue; our CTM has it’s own upscaling capability, by means of traffic, computing, storing and managing itself. It is also designed failsafe for high availability, placed on cloud, on different geographic locations. We know the requirements for being best and we tried harder for it.
 CAT – Central Attack Trap
CAT – Central Attack Trap
What we serve with CAT and it’s subsystems are stated below.
– Tracking Roaming Files and Inspecting Local Files : Although using different detection systems for file-based attacks by e-mail filters, firewall spam filters, antivirus scanners etc. still, files are complicated threats in a network environment. In order to eliminate file threats, you still have to track roaming files in Internet, classify them as harming / unharming clean files, even detect their true intention (!) because they can be coded for hiding harming intention. It is a team job actually, which we also covered it.
– Hyperactive Threat Inspection : Determining a recently started attack; gathering it’s details and applying prevention just before it spreads? It is a security pro-work. We got it covered.
– Attacker Call-Back Traffic Analysis : Determining a traffic started unintentionally and/or without user knowledge even hiding itself in many ways; we can detect it. It doesn’t matter if it is a known hacker traffic, included in any databases, or an unknown zero-day attack, without privacy violation, we are ready to analyze it automated and on the fly. It is a security pro-work. We got it covered.
CAT Subsystems
Global Honeynet
- Trapped vulnerable systems for detection of bots and attackers that are searching for vulnerabilities in Internet.
- Collects spams and/or targeted e-mails towards strategic sectors and forwards to CSI for further analysis.
- Works interactive with CTM and activates traps by subject tracking if necessary.
Enhanced Domain Inspector (EDI)
- Extensive server observation and inspection system detects threat by scoring, even the server may not implicated for a crime yet
- Detects (region-specific only) phishing-based attacks even before crime elements created yet
- Runs automatic scans on accessible Internet fields and deep Internet (deepweb) fields
CAT Technical Specifications
Worldwide spread honeynet, simulated servers for gathering attacks, numerous datasets for a better EDI scoring…
We won’t give you exact numbers, sorry, but let us give a little clue; our CAT has it’s own specific sectors settled around the world and 7/24 actively collecting info from various databases even underground (deepweb) systems and managing itself. It is designed for high availability, placed on cloud, on different geographic locations. We know the requirements for being best and we tried harder for it.
 CSI – Central Sandbox Inspection
CSI – Central Sandbox Inspection
What we serve with CSI and it’s subsystems are stated below.
– Tracking Roaming Files and Inspecting Local Files : Although using different detection systems for file-based attacks by e-mail filters, firewall spam filters, antivirus scanners etc. still, files are complicated threats in a network environment. In order to eliminate file threats, you still have to track roaming files in Internet, classify them as harming / unharming clean files, even detect their true intention (!) because they can be coded for hiding harming intention. It is a team job actually, which we also covered it.
– Hyperactive Threat Inspection : Determining a recently started attack; gathering it’s details and applying prevention just before it spreads? It is a security pro-work. We got it covered.
– Live Traffic Analysis : Inspecting a traffic without violating user privacy is a sensitive issue. Without gathering all the user traffic information and analyzing user trends, which is a violation of privacy ethics, we do analyze connection protocol behaviors and following created unintentional connections towards an Internet address. It doesn’t matter if it is a new site or a cached site, even it isn’t included in any databases, a recently started traffic is analyzed on the fly; without privacy violation, and determined either intentional or unintentional connection. It is a security pro-work. We got it covered.
– Attacker Call-Back Traffic Analysis : Determining a traffic started unintentionally and/or without user knowledge even hiding itself in many ways; we can detect it. It doesn’t matter if it is a known hacker traffic, included in any databases, or an unknown zero-day attack, without privacy violation, we are ready to analyze it automated and on the fly. It is a security pro-work. We got it covered.
CSI Subsystems
Feeds other TINA systems and technologies with central analysis, including both automated and supervised laboratory analysis.
Multiple Structure
- Can examine more than one layer as; static analysis, dynamic analysis (sandbox), behavior analysis
- Besides file analysis, includes link and code tracking features on it’s analysis
Monitoring and Support System
- Analyzes data received from the CAT System and suspicious data demanded by TINA appliances.
- Follows the links within the e-mails and analyzes
Data Privacy and Protection
- Protects data privacy; does not share any personal data, does not transfer out any personal data, does not analyze private data
- Does not store any instance of files on sandbox analysis
Prevention Techniques Against Anti-Sandbox
- Accommodates prevention techniques against anti-sanboxing technologies
- Sandbox analysis are operated on actual operating systems
CSI Technical Specifications
How many files can we analyze concurrently? How many could you send? Send as many as you can! Faster to full analysis, non-stop analysis of threat objects.
We won’t give you exact numbers, sorry, but let us give a little clue; our CAT has it’s own upscaling capacity, by means of traffic, computing, storing and managing itself. Not only analyzes your files, also analyzes roaming objects on Internet around the world, 7/24 actively. It is designed for high availability, placed on cloud, on different geographic locations. We know the requirements for being best and we tried harder for it.
 TPI – TINA Packet Inspection
TPI – TINA Packet Inspection
What we serve with TPI and it’s subsystems are stated below.
– Tracking and Applying Threat Databases : Inspecting online databases, evaluating the threats and selecting and applying the necessary rules to prevent threats is a must for a security employee. There are a few challenges; one of them is doing it as soon as possible, so the intruders won’t be able to use known threats against you, and second challenge is to do it 24 hours a day in whole 7 week days, whole year (!), without stopping. It ain’t a human’s job, right? We covered it.
– Live Traffic Analysis : Inspecting a traffic without violating user privacy is a sensitive issue. Without gathering all the user traffic information and analyzing user trends, which is a violation of privacy ethics, we do analyze connection protocol behaviors and following created unintentional connections towards an Internet address. It doesn’t matter if it is a new site or a cached site, even it isn’t included in any databases, a recently started traffic is analyzed on the fly; without privacy violation, and determined either intentional or unintentional connection. It is a security pro-work. We got it covered.
– Attacker Call-Back Traffic Analysis : Determining a traffic started unintentionally and/or without user knowledge even hiding itself in many ways; we can detect it. It doesn’t matter if it is a known hacker traffic, included in any databases, or an unknown zero-day attack, without privacy violation, we are ready to analyze it automated and on the fly. It is a security pro-work. We got it covered.
TPI Subsystems
Feeds other TINA systems and technologies with local analysis, including both on the fly and automated follow-up laboratory analysis.
Instant Crime Analysis (ICA)
- Enhanced package inspection technology that analysis protocols.
- Equipped with artificial intelligence-based classification skills.
- Can detect the addresses involved in the crime.
- Can analyze and detect malicious command and control center of malware (C&C).
- Monitors and analysis the domain name queries on the network.
- Besides it’s own technologies, uses antivirus & antimalware and various 3rd party data bases to detect harmful data traffic.
Instant Correlation Engine (ICE)
- Enables interaction with Instant Crime Analysis and other modules.
- Maps and benchmarks with databases.
Instant Interception Firewall (IIF)
- Enables the implementation of decisions derived from TINA’s automation, performs the automated firewall blocking of traffic and isolation decisions.
- Controls traffic preventing, forwarding and client isolation when needed.
- Emergency response option; Turns off all the ports through external network and just enables basic ports (Web and/or e-mail) open.
- Prevents the execution of basic remote shell code’s.
TPI Technical Specifications
How many connections can we analyze concurrently? How many do you need? We can speed up to 1Gbps! Surf as many as you can!
We have quicker to full analysis lead by dynamic managing during analysis, non-stop; so our concurrent limit is always higher than your requirements.
We won’t give you exact numbers, sorry, but let us give a little clue; our TPI has it’s own capacity manager system in it, by means of traffic, we do 1Gbps in 1 seconds. We do not use our hardware capacity more than 50% in full load, by all means; computing, storing and managing. We have hardware bypass and software precautions (we give detailed infos only to TINA owners). We know the requirements for being best and we tried harder for it.
 LAT – Local attack Trap
LAT – Local attack Trap
What we serve with LAT and it’s subsystems are stated below.
– Hyperactive Threat Inspection : Determining a recently started attack; gathering it’s details and applying prevention just before it spreads? It is a security pro-work. We got it covered.
– Live Traffic Analysis : Inspecting a traffic without violating user privacy is a sensitive issue. Without gathering all the user traffic information and analyzing user trends, which is a violation of privacy ethics, we do analyze connection protocol behaviors and following created unintentional connections towards an Internet address. It doesn’t matter if it is a new site or a cached site, even it isn’t included in any databases, a recently started traffic is analyzed on the fly; without privacy violation, and determined either intentional or unintentional connection. It is a security pro-work. We got it covered.
– Attacker Call-Back Traffic Analysis : Determining a traffic started unintentionally and/or without user knowledge even hiding itself in many ways; we can detect it. It doesn’t matter if it is a known hacker traffic, included in any databases, or an unknown zero-day attack, without privacy violation, we are ready to analyze it automated and on the fly. It is a security pro-work. We got it covered.
LAT Subsystems
Feeds other TINA systems and technologies with local analysis, including both on the fly and automated follow-up laboratory analysis.
Honeypot Services (HS)
- Identifies and informs about activities against servers.
- Detects and stops malicious malware and attacker activity on the network either already activated or trying to become active.
- Detects and reports endpoint addresses of command and control centers (C&C) of malware and/or attacker
LAT Technical Specifications
How many connections can we analyze concurrently? How many do you need? We can speed up to 1Gbps! Surf as many as you can!
We have various analyze types lead by TINA AI during analysis, by non-stop dynamic managing our concurrent limit is always higher than your requirements.
We won’t give you exact numbers, sorry, but let us give a little clue; our LAT has it’s own capacity manager system in it, by means of traffic, we do 1Gbps in 1 seconds. We do not use our hardware capacity more than 50% in full load, by all means; computing, storing and managing. We have hardware bypass and software precautions (we give detailed infos only to TINA owners). We know the requirements for being best and we tried harder for it.
 PAI – Protocol Analysis Inspection
PAI – Protocol Analysis Inspection
What we serve with PAI and it’s subsystems are stated below.
– Hyperactive Threat Inspection : Determining a recently started attack; gathering it’s details and applying prevention just before it spreads? It is a security pro-work. We got it covered.
– Live Traffic Analysis : Inspecting a traffic without violating user privacy is a sensitive issue. Without gathering all the user traffic information and analyzing user trends, which is a violation of privacy ethics, we do analyze connection protocol behaviors and following created unintentional connections towards an Internet address. It doesn’t matter if it is a new site or a cached site, even it isn’t included in any databases, a recently started traffic is analyzed on the fly; without privacy violation, and determined either intentional or unintentional connection. It is a security pro-work. We got it covered.
– Attacker Call-Back Traffic Analysis : Determining a traffic started unintentionally and/or without user knowledge even hiding itself in many ways; we can detect it. It doesn’t matter if it is a known hacker traffic, included in any databases, or an unknown zero-day attack, without privacy violation, we are ready to analyze it automated and on the fly. It is a security pro-work. We got it covered.
– Attacker On Initial Phase Prevention : Even all of your prevention techniques and detection techniques fail; we do help for fighting back! An attacker after infiltrating to the network needs to map it; finding valuable server assets or stating the size of a network, we are there to confuse and stop the attack. We can detect mapping intentions and prevent it. Furthermore, we analyze the traffic back to the attacker and stop sequel traffic on the fly. We got it covered.
PAI Subsystems
Feeds other TINA systems and technologies with local analysis, including both on the fly and automated follow-up laboratory analysis.
- Most advanced Tina technology which enables detection of APTs with high ratio. It’s a unique technology that uses protocol analysis for detecting and following suspicious connections either a new or an established connection. Works even it is a secured (SSL/TLS) connection.
- Available in two separate modes;
- Advanced PAI: protocol follows suspicious connections
- Active PAI: protocol follows all connections
PAI Technical Specifications
How many connections can we analyze concurrently? How many do you need? We can speed up to 1Gbps! Surf as many as you can!
We have the control with TINA AI, by dynamic managing during analysis, non-stop we manage the resources, so our concurrent limit is always higher than your requirements.
We won’t give you exact numbers, sorry, but let us give a little clue; our PAI has it’s own capacity manager system in it, by means of traffic, we do 1Gbps in 1 seconds. We do not use our hardware capacity more than 50% in full load, by all means; computing, storing and managing. We have hardware bypass and software precautions (we give detailed infos only to TINA owners). We know the requirements for being best and we tried harder for it.
 LSI – Local Static Inspection
LSI – Local Static Inspection
What we serve with LSI and it’s subsystems are stated below.
– Tracking Roaming Files and Inspecting Local Files : Although using different detection systems for file-based attacks by e-mail filters, firewall spam filters, antivirus scanners etc. still, files are complicated threats in a network environment. In order to eliminate file threats, you still have to track roaming files in Internet, classify them as harming / unharming clean files, even detect their true intention (!) because they can be coded for hiding harming intention. It is a team job actually, which we also covered it.
– Hyperactive Threat Inspection : Determining a recently started attack; gathering it’s details and applying prevention just before it spreads? It is a security pro-work. We got it covered.
– Live Traffic Analysis : Inspecting a traffic without violating user privacy is a sensitive issue. Without gathering all the user traffic information and analyzing user trends, which is a violation of privacy ethics, we do analyze connection protocol behaviors and following created unintentional connections towards an Internet address. It doesn’t matter if it is a new site or a cached site, even it isn’t included in any databases, a recently started traffic is analyzed on the fly; without privacy violation, and determined either intentional or unintentional connection. It is a security pro-work. We got it covered.
LSI Subsystems
Feeds other TINA systems and technologies with local analysis, including both on the fly and automated follow-up laboratory analysis.
- Most advanced Tina technology which enables detection of APTs with high ratio. It’s a unique technology that uses protocol analysis for detecting and following suspicious connections either a new or an established connection. Works even it is a secured (SSL/TLS) connection.
- Available in two separate modes;
- Advanced PAI: protocol follows suspicious connections
- Active PAI: protocol follows all connections
LSI Technical Specifications
How many files can we analyze concurrently? How many do you need? We have limits that can expand!
We have a quicker analysis algorithm lead by dynamic managing during analysis, but there is a concurrent limit.
We can expand our systems for much higher file requirements.
We won’t give you exact numbers, sorry, for users with enormous file amounts, our LSI system have expandable hardware options, also can run multiple LSI units in one location, fully compatible with other TINA systems. We have bypass and software precautions (we give detailed infos only to TINA owners). We know the requirements for being best and we tried harder for it.